比如做百度知道 .html,这些都是我们不可控制的网站!谷歌三件套下载
漏洞处理方法:
1、可以使用系统防火墙
来做限制只允许ES集群和Server节点的IP来访问漏洞节点的9200端口,其他的全部拒绝。
2、在ES节点上设置用户密码
漏洞现象:直接访问9200端口不需要密码验证
修复过程
2.1 生成认证文件
必须要生成认证文件,且ES配置文件里要引用这些生成的认证文件,否则启动ES的时候,日志会报错:Caused by: javax.net.ssl.SSLHandshakeException: No available authentication scheme。
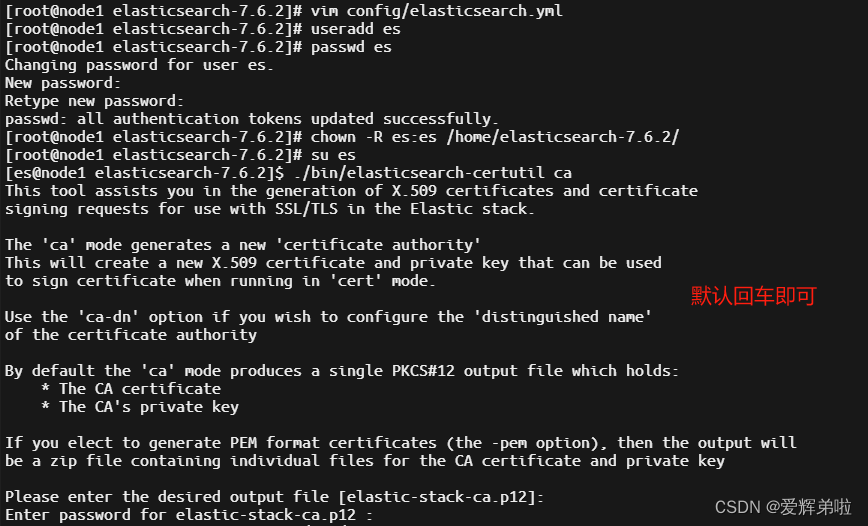
CA 证书
[root@node1 elasticsearch-7.6.2]# su es
[es@node1 elasticsearch-7.6.2]$ ./bin/elasticsearch-certutil ca
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.The 'ca' mode generates a new 'certificate authority'
This will create a new X.509 certificate and private key that can be used
to sign certificate when running in 'cert' mode.Use the 'ca-dn' option if you wish to configure the 'distinguished name'
of the certificate authorityBy default the 'ca' mode produces a single PKCS#12 output file which holds:* The CA certificate* The CA's private keyIf you elect to generate PEM format certificates (the -pem option), then the output will
be a zip file containing individual files for the CA certificate and private keyPlease enter the desired output file [elastic-stack-ca.p12]:
Enter password for elastic-stack-ca.p12 :
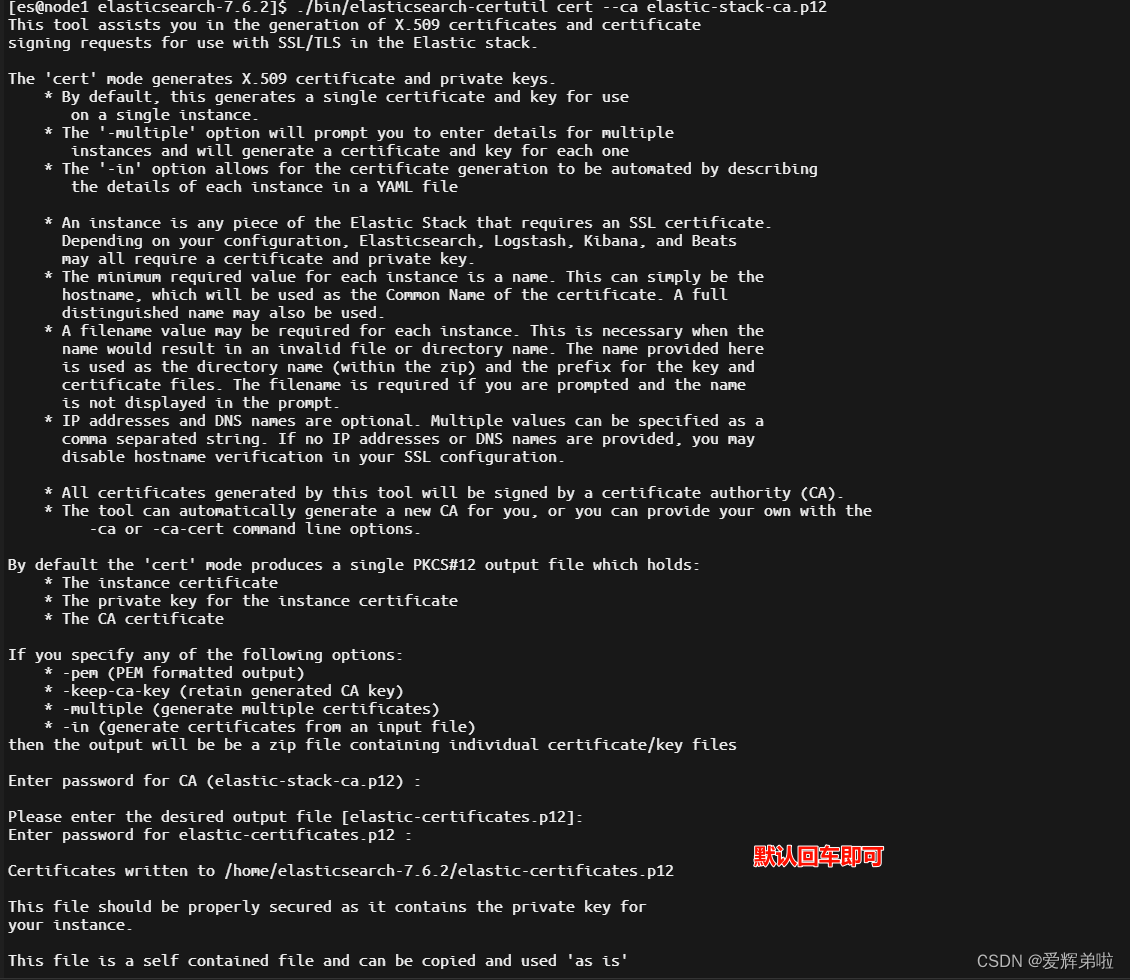
2.2 生成p12密钥
使用第一步生成的证书,生成p12秘钥
[es@node1 elasticsearch-7.6.2]$ ./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.The 'cert' mode generates X.509 certificate and private keys.* By default, this generates a single certificate and key for useon a single instance.* The '-multiple' option will prompt you to enter details for multipleinstances and will generate a certificate and key for each one* The '-in' option allows for the certificate generation to be automated by describingthe details of each instance in a YAML file* An instance is any piece of the Elastic Stack that requires an SSL certificate.Depending on your configuration, Elasticsearch, Logstash, Kibana, and Beatsmay all require a certificate and private key.* The minimum required value for each instance is a name. This can simply be thehostname, which will be used as the Common Name of the certificate. A fulldistinguished name may also be used.* A filename value may be required for each instance. This is necessary when thename would result in an invalid file or directory name. The name provided hereis used as the directory name (within the zip) and the prefix for the key andcertificate files. The filename is required if you are prompted and the nameis not displayed in the prompt.* IP addresses and DNS names are optional. Multiple values can be specified as acomma separated string. If no IP addresses or DNS names are provided, you maydisable hostname verification in your SSL configuration.* All certificates generated by this tool will be signed by a certificate authority (CA).* The tool can automatically generate a new CA for you, or you can provide your own with the-ca or -ca-cert command line options.By default the 'cert' mode produces a single PKCS#12 output file which holds:* The instance certificate* The private key for the instance certificate* The CA certificateIf you specify any of the following options:* -pem (PEM formatted output)* -keep-ca-key (retain generated CA key)* -multiple (generate multiple certificates)* -in (generate certificates from an input file)
then the output will be be a zip file containing individual certificate/key filesEnter password for CA (elastic-stack-ca.p12) : Please enter the desired output file [elastic-certificates.p12]:
Enter password for elastic-certificates.p12 : Certificates written to /home/elasticsearch-7.6.2/elastic-certificates.p12This file should be properly secured as it contains the private key for
your instance.This file is a self contained file and can be copied and used 'as is'
For each Elastic product that you wish to configure, you should copy
this '.p12' file to the relevant configuration directory
and then follow the SSL configuration instructions in the product guide.For client applications, you may only need to copy the CA certificate and
configure the client to trust this certificate.
2.3 将p12认证文件copy到其他节点
[es@node1 elasticsearch-7.6.2]$ cd config/
[es@node1 config]$ ll
total 36
-rw-rw---- 1 es es 3284 Dec 14 07:49 elasticsearch.yml
-rw-rw---- 1 es es 2301 Mar 26 2020 jvm.options
-rw-rw---- 1 es es 17545 Mar 26 2020 log4j2.properties
-rw-rw---- 1 es es 473 Mar 26 2020 role_mapping.yml
-rw-rw---- 1 es es 197 Mar 26 2020 roles.yml
-rw-rw---- 1 es es 0 Mar 26 2020 users
-rw-rw---- 1 es es 0 Mar 26 2020 users_roles
[es@node1 config]$ mkdir certs
[es@node1 config]$ cp ../elastic-certificates.p12 certs/
[root@node1 elasticsearch-7.6.2]# scp -r config node2:/home/elasticsearch-7.6.2/
log4j2.properties 100% 17KB 12.2MB/s 00:00
users_roles 100% 0 0.0KB/s 00:00
roles.yml 100% 197 406.7KB/s 00:00
users 100% 0 0.0KB/s 00:00
role_mapping.yml 100% 473 1.0MB/s 00:00
elasticsearch.yml 100% 3284 3.2MB/s 00:00
jvm.options 100% 2301 4.4MB/s 00:00
elastic-certificates.p12 100% 3443 3.1MB/s 00:00
[root@node1 elasticsearch-7.6.2]# scp -r config node3:/home/elasticsearch-7.6.2/
log4j2.properties 100% 17KB 14.6MB/s 00:00
users_roles 100% 0 0.0KB/s 00:00
roles.yml 100% 197 492.4KB/s 00:00
users 100% 0 0.0KB/s 00:00
role_mapping.yml 100% 473 1.1MB/s 00:00
elasticsearch.yml 100% 3284 2.7MB/s 00:00
jvm.options 100% 2301 5.0MB/s 00:00
elastic-certificates.p12 100% 3443 3.9MB/s 00:00
[root@node1 elasticsearch-7.6.2]#
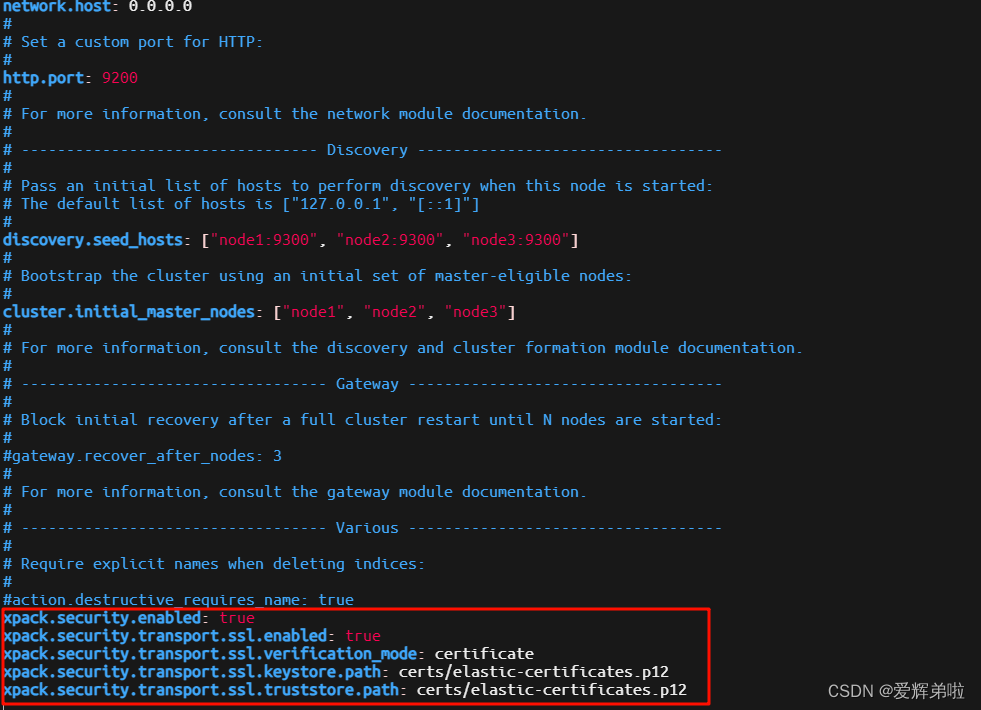
2.4 修改所有ES节点配置文件
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: certs/elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: certs/elastic-certificates.p12
2.5 启动集群各节点
[es@node1 elasticsearch-7.6.2]$ ./bin/elasticsearch -d
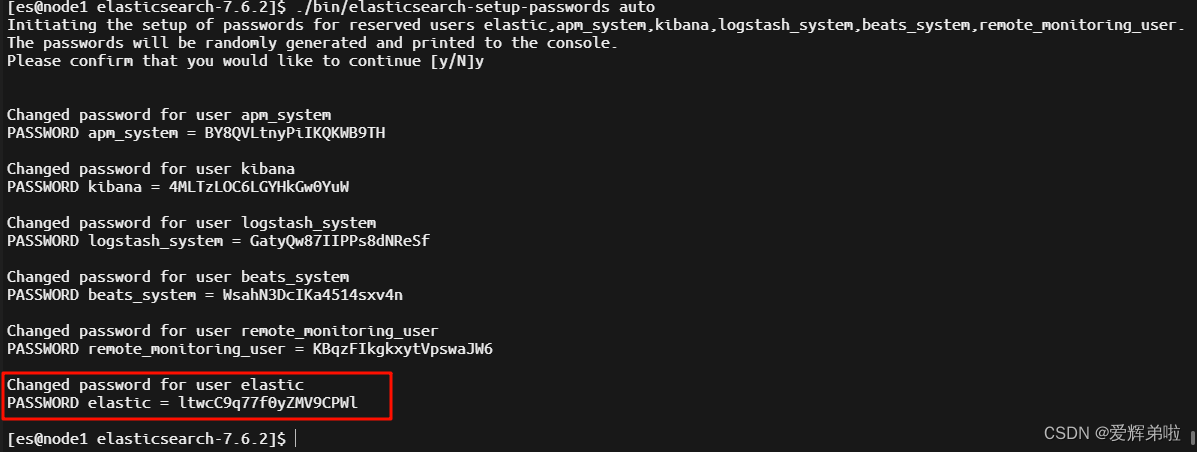
2.6 自动生成密码
集群也是一台节点生成密码即可
[es@node1 elasticsearch-7.6.2]$ ./bin/elasticsearch-setup-passwords auto
Initiating the setup of passwords for reserved users elastic,apm_system,kibana,logstash_system,beats_system,remote_monitoring_user.
The passwords will be randomly generated and printed to the console.
Please confirm that you would like to continue [y/N]yChanged password for user apm_system
PASSWORD apm_system = BY8QVLtnyPiIKQKWB9THChanged password for user kibana
PASSWORD kibana = 4MLTzLOC6LGYHkGw0YuWChanged password for user logstash_system
PASSWORD logstash_system = GatyQw87IIPPs8dNReSfChanged password for user beats_system
PASSWORD beats_system = WsahN3DcIKa4514sxv4nChanged password for user remote_monitoring_user
PASSWORD remote_monitoring_user = KBqzFIkgkxytVpswaJW6Changed password for user elastic
PASSWORD elastic = ltwcC9q77f0yZMV9CPWl[es@node1 elasticsearch-7.6.2]$
3、验证漏洞是否修复成功
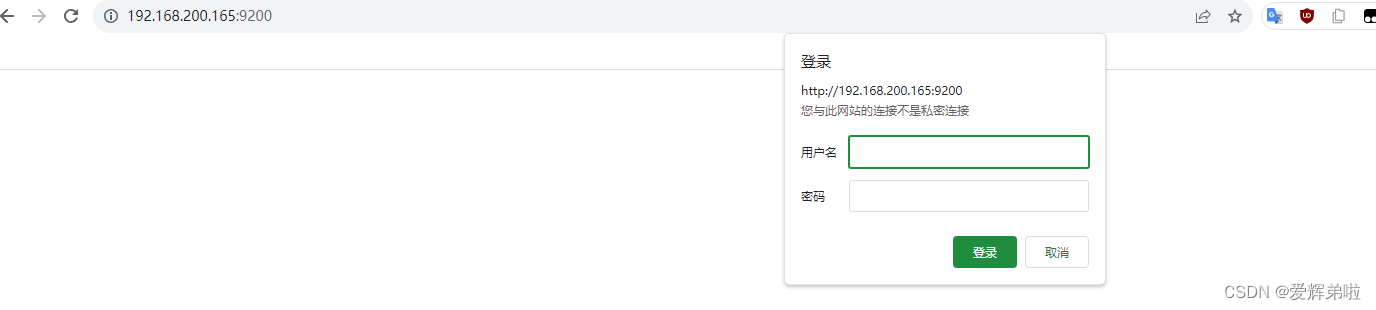
[es@node1 elasticsearch-7.6.2]$ curl http://192.168.200.167:9200/_cat/indices?pretty -u elastic
